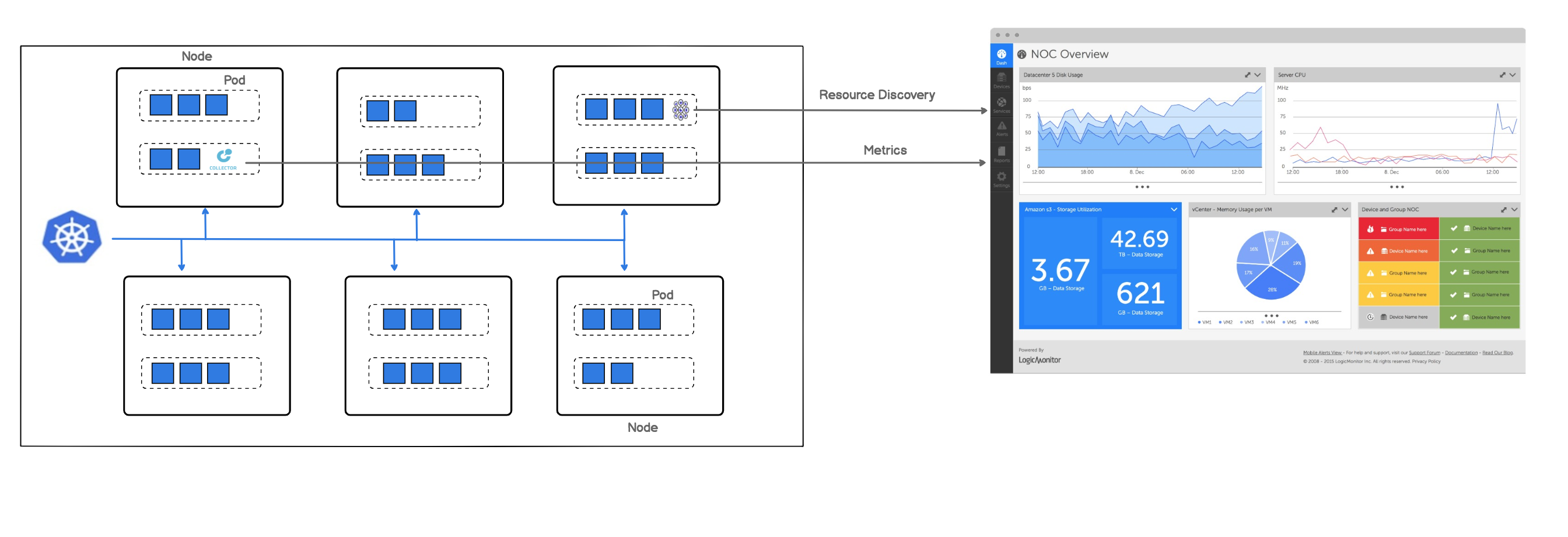
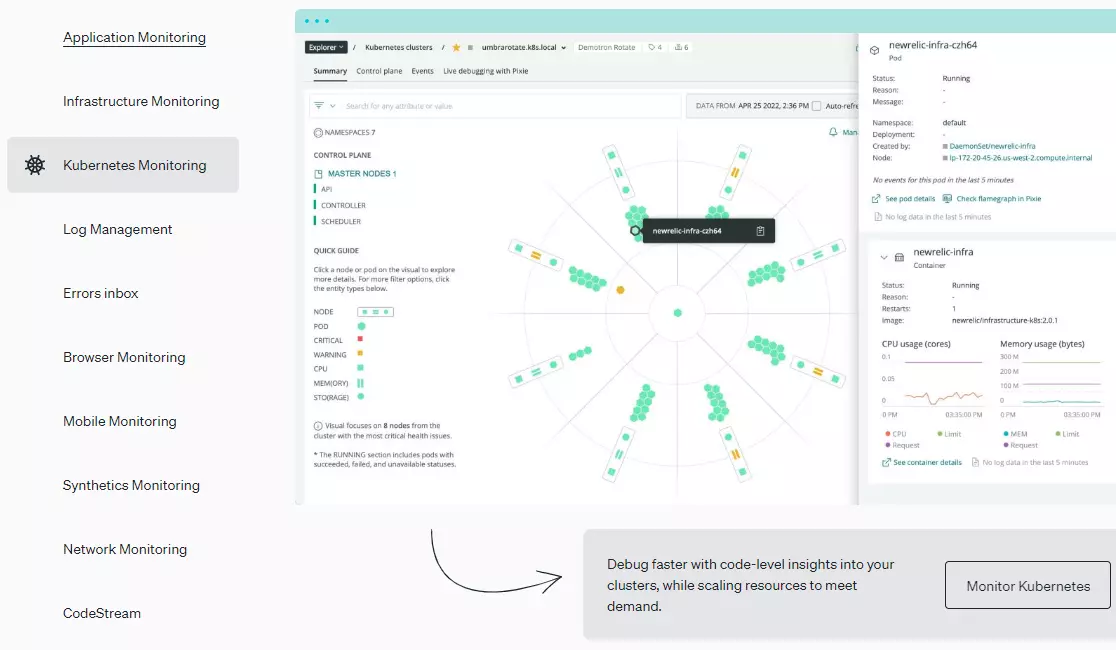
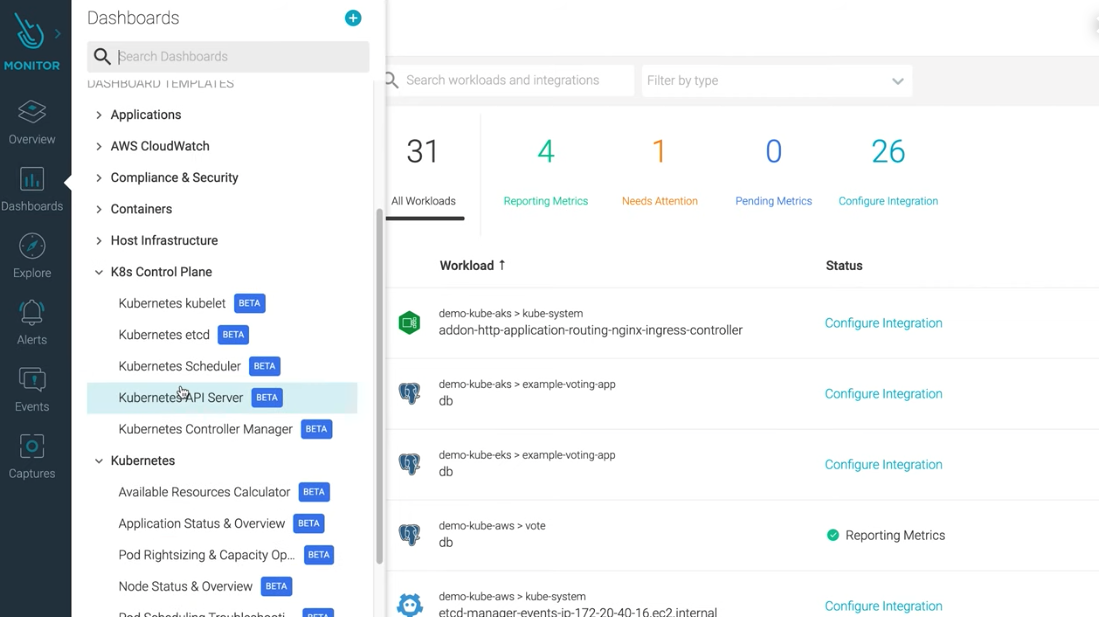
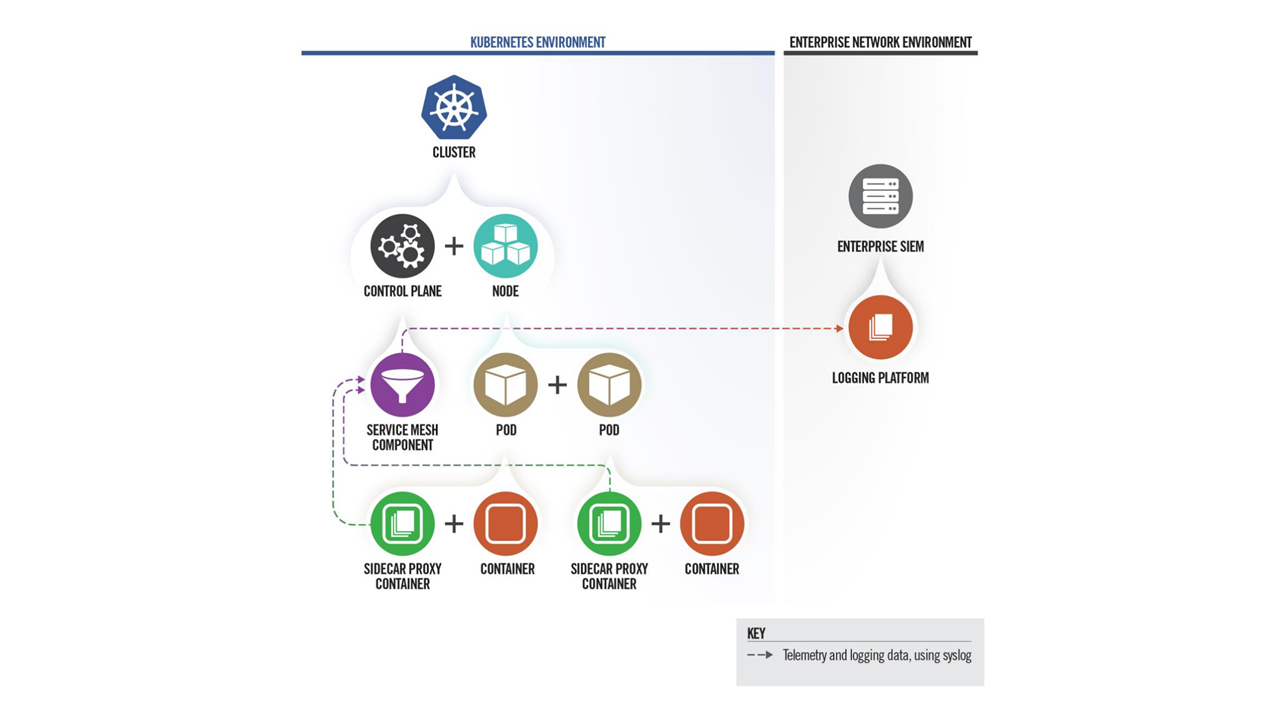
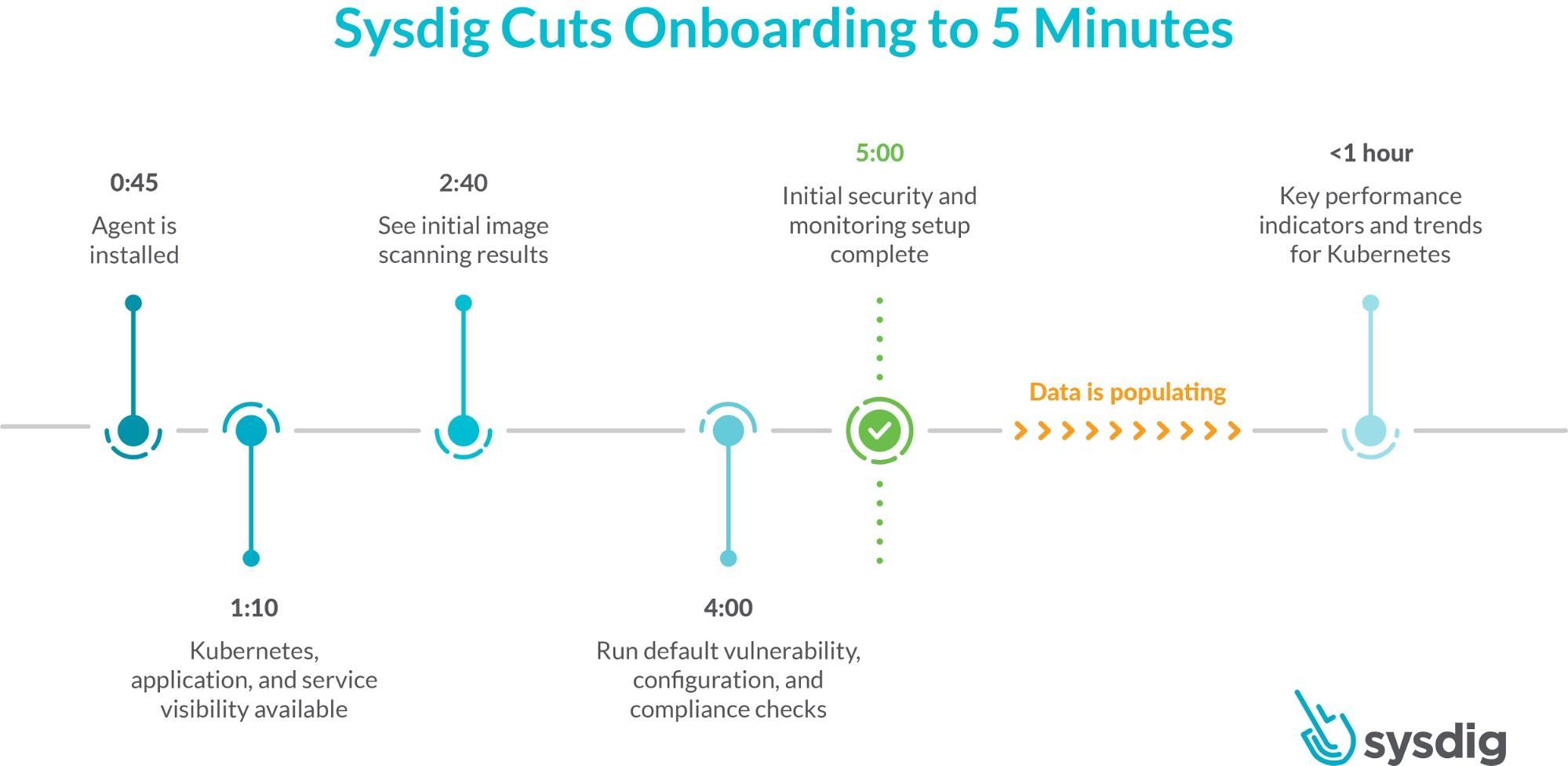
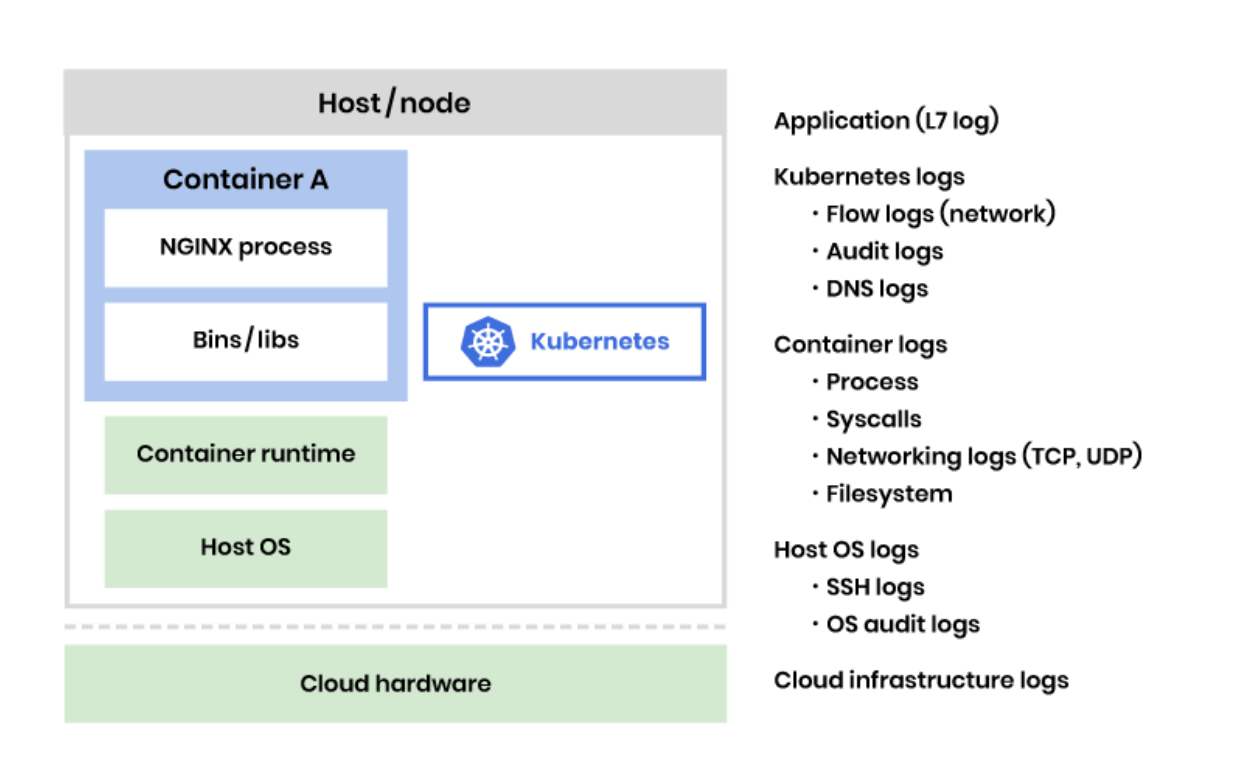
2 Widespread Attacks on Your Containerized Environment and 7 Rules to Prevent it. | by Boris Zaikin | ITNEXT

Kubernetes Security in 2024: 5 Hacks to Safeguard Your Clusters | by Srisainath | Jan, 2024 | Medium

Pro Google Kubernetes Engine: Network, Security, Monitoring, and Automation Configuration 1st ed., Sabharwal, Navin, Pandey, Piyush, Pandey, Piyush, eBook - Amazon.com


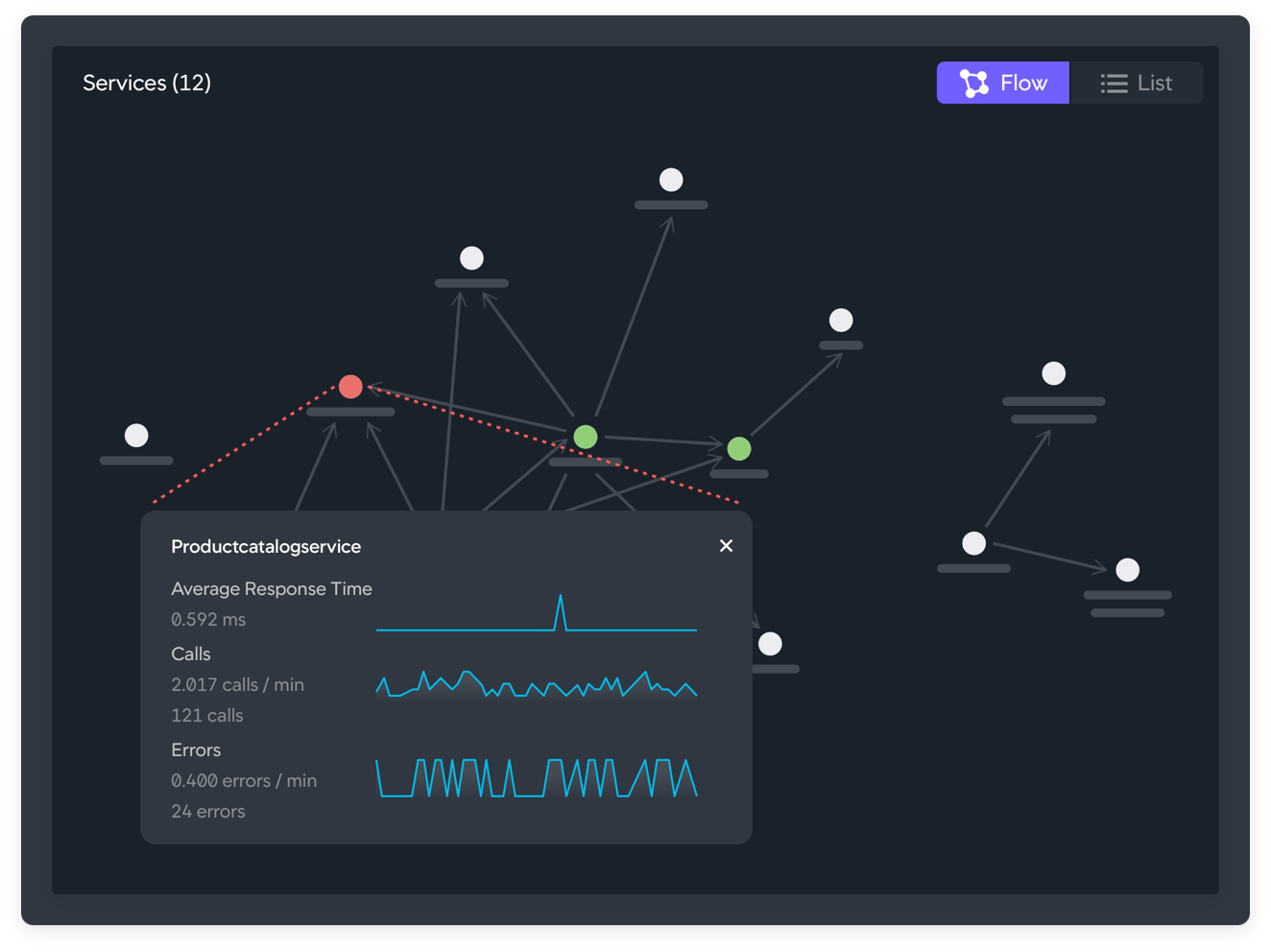
![Kubernetes dashboard | Elastic Security Solution [8.12] | Elastic Kubernetes dashboard | Elastic Security Solution [8.12] | Elastic](https://www.elastic.co/guide/en/security/current/images/kubernetes-dashboard.png)