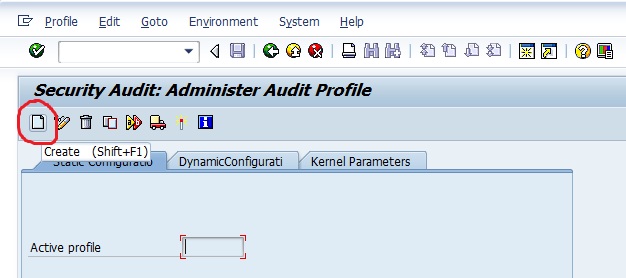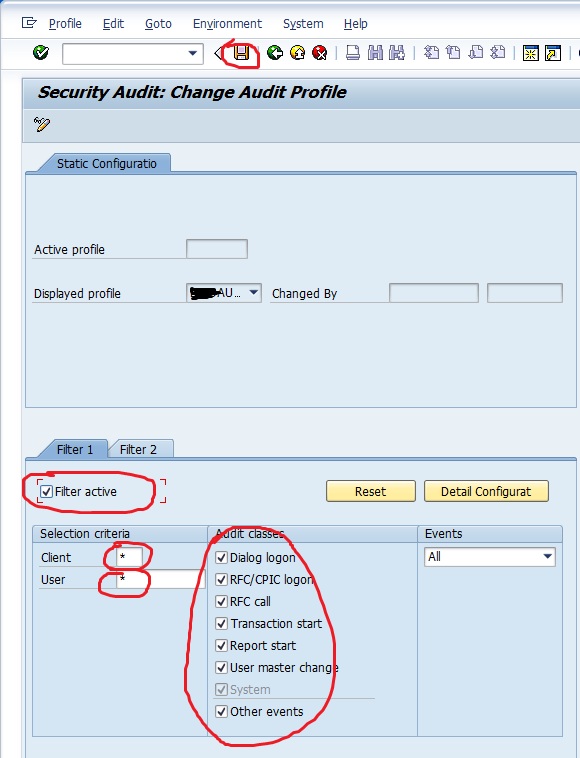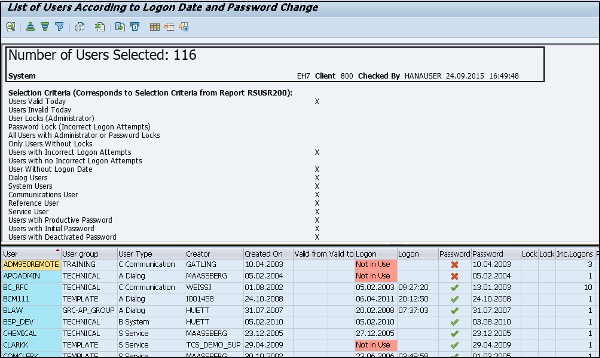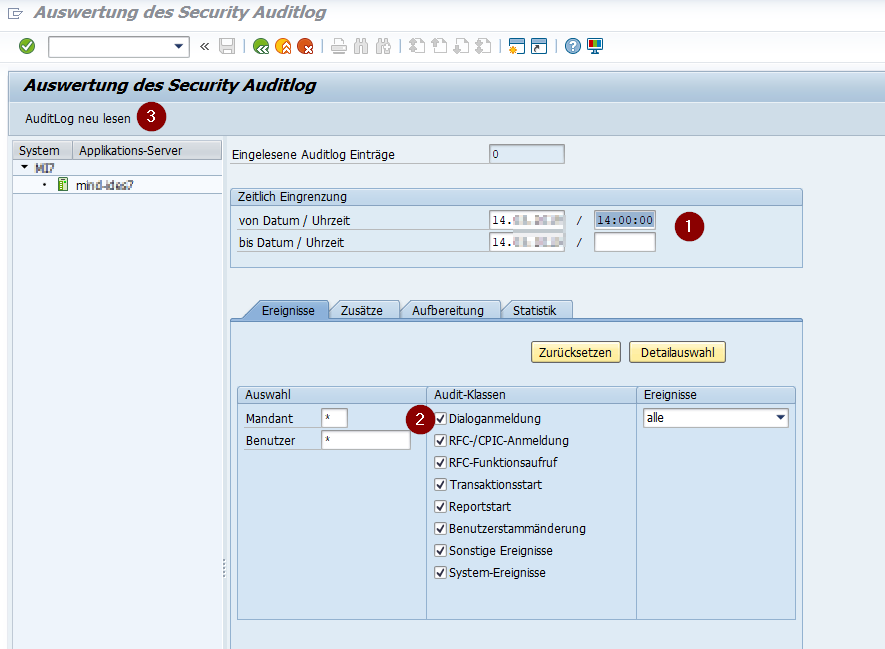
SAP Security Audit Log Retention and Storage | SAP security | Enterprise threat detection for SAP | ETD | realtime SAP monitoring | ETM | SAP Splunk | SAP HP ArcSight

Analysis and Recommended Settings of the Security Audit Log (SM19 / RSAU_CONFIG, SM20 / RSAU_READ_LOG) | SAP Blogs